
Locky Ransomware – What you need to know!
While the name ‘locky’ seems like a rather benign or cheerful name for a ransomware threat, the malware itself is no joke.
This particular threat is so named because it renames all your files with a ‘.locky’ file extension – after it encrypts them so they are unable to be used by whichever program they are associated with.
After the malware has done its work – you’ll be notified that you can buy the decryption key from the ‘dark web’.
Prices for the key seem to vary between 0.5 BTC (bitcoin) and 1.00 BTC. One BTC is currently about $400, so your unlock key will run you somewhere from $200 to $400.
The most common way to receive the threats are:
- You receive an email containing an attached document (Troj/DocDl-BCF).
- The document looks like gobbledegook.
- The document advises you to enable macros “if the data encoding is incorrect.”
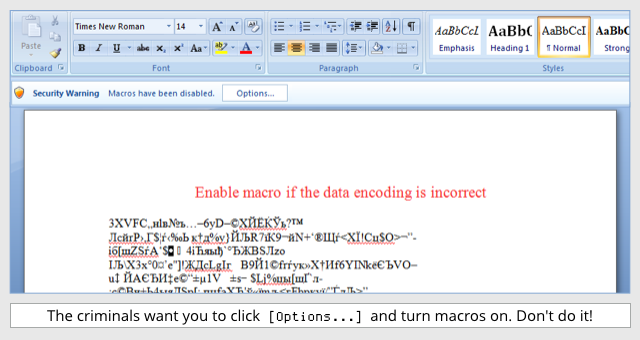
- If you enable macros, you don’t actually correct the text encoding (that’s a subterfuge); instead, you run code inside the document that saves a file to disk and runs it.
- The saved file (Troj/Ransom-CGX) serves as a downloader, which fetches the final malware payload from the crooks.
- The final payload could be anything, but in this case is usually the Locky Ransomware (Troj/Ransom-CGW).
Locky scrambles all files that match a long list of extensions, including videos, images, source code, and Office files.
Locky even scrambles wallet.dat, your Bitcoin wallet file, if you have one – locking you out of your bitcoin funds.
In other words, if you have more BTCs in your wallet than the cost of the ransom, and no backup, you are highly likely to pay up. (And you’ll already know how to buy new bitcoins, and how to pay with them.)
Locky will also remove any Volume Snapshot Service (VSS) files, also known as shadow copies, that you may have made. This means you have no windows snapshot ‘backup files’.
Shadow copies are the Windows way of making live backup snapshots without having to stop working – you don’t need to logout or even close your applications first – so they are a quick and popular alternative to a proper backup procedure. Locky Ransomware nullifies this ‘backup’ method.
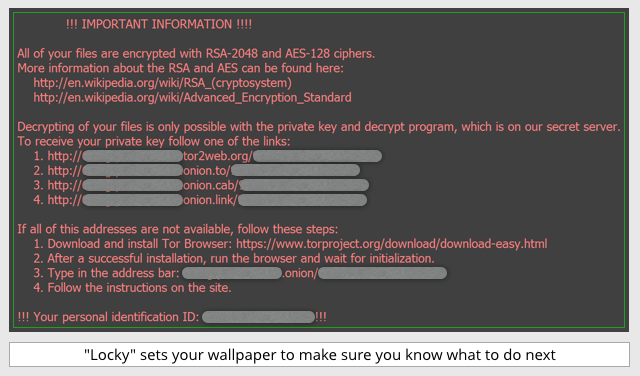
If you visit the dark web page given in the warning message, you receive the instructions for payment shown above.
Unfortunately, there are no apparent shortcuts to get your data back if you don’t have a recent backup to be able to restore from.
Remember, also, that like most ransomware, Locky ransomware doesn’t just scramble your C: drive.
It scrambles any files in any directory on any mounted drive that it can access, including removable drives that are plugged in at the time, or network shares that are accessible to your machine, including servers and other people’s computers, whether they are running Windows, OS X or Linux. No files on accessible drives are safe from encryption.
If you are logged in as a domain administrator and you get hit by ransomware, you could do very widespread damage to your network environment.
Giving yourself up front all the login power you might ever need is very convenient, but please don’t do it. Running as an administrator on your domain is a recipe for disaster.
Only login (or use Run As…) with admin powers when you really need them, and relinquish those powers as soon as you don’t.
WHAT TO DO?
- Backup your system regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Don’t give yourself more login power than you need. Most importantly, don’t stay logged in as an administrator any longer than is strictly necessary, and avoid browsing, opening documents or other “regular work” activities while you have administrator rights.
- Consider installing the Microsoft Office viewers. These viewer applications let you see what documents look like without opening them in Word or Excel itself. In particular, the viewer software doesn’t support macros at all, so you can’t enable macros by mistake!
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit.
Hopefully these tips will help you stay safe from not just the Locky Ransomware, but other emerging forms of Ransomware which we expect to see in the coming weeks, months and years.
